There are a lot of tools available for blocking ads, removing
spyware, scanning for viruses. Most of this unwanted content comes from
known ad servers and known malicious websites.
The Windows HOSTS file allows you to block some of this content very easily and for free. However, this is not a complete internet security solution. It is still recommended that you run anti-virus software on your computer and be careful of the websites you visit.
Windows 7, Windows Vista, Windows XP, Windows Server 2003:
C:\WINDOWS\system32\drivers\etc
Windows 2000:
C:\WINNT\system32\drivers\etc\
Windows 98/ME:
C:\WINDOWS
The HOSTS file does not have an extension, but it is a plain text file. This file allows you to manually associate IP addresses with domain names (i.e., google.com) so the Domain Name Server (DNS) can quickly resolve an address.
To use the HOSTS file to block a website, assign the IP address of 127.0.0.1 to the domain name of known ad servers and malicious websites. 127.0.0.1 is the IP address of your local computer, if you chose to run a server on it.
As an example, let’s say some ad server hosts a banner ad at the URL: http://www.adsite.com/ads/12345.jpg. If you associate this domain name with the IP address of your local computer, 127.0.0.1, when that website tries to load that image, it will not be found because the image file does not exist on your computer. Therefore, the ad will not display on that webpage.
That tells the rest of the file that 127.0.0.1 is your local machine, as mentioned above. You could also use 0.0.0.0 instead of 127.0.0.1 — either will work. However, whichever IP address you use for localhost, also use for the sites you want to block.
After the localhost entry, enter known ad servers and malicious websites and assign your local IP address to each domain name. Put the IP address at the beginning of the line, followed by a tab, followed by the domain name for the ad server or malicious website. Here’s an example of the HOSTS file:

NOTE: Some spyware programs automatically add ad servers and malicious websites to your HOSTS file for you.
Therefore, before you save a big list of ad servers and malicious websites in the HOSTS file, select Control Panel | Administrative Tools | Services from the Start menu.

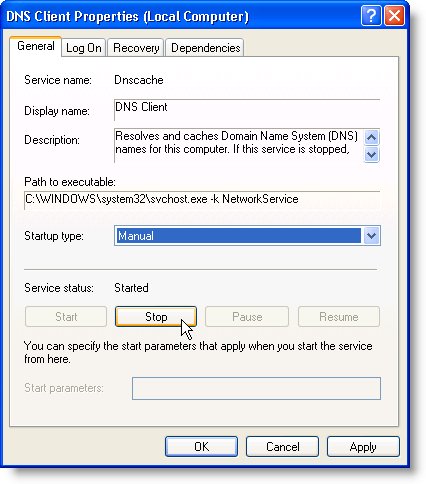
Scroll down to the DNS Client service, right-click on it, and select Properties from the pop-up menu.

The DNS Client Properties dialog box displays. Select Manual from the Startup type drop-down list. Click Stop below Service status to stop the service. Click Apply and then click OK.

For more information about the HOSTS file, see http://accs-net.com/hosts/what_is_hosts.html. You can find maintained HOSTS files online or start to build your own. See http://www.mvps.org/winhelp2002/hosts.htm to download a good, free, pre-populated HOSTS file.
There is a .zip file for download containing the HOSTS file, a batch file for easy installation, and a readme file with instructions for installation in the different versions of Windows. Beware that there are special instructions for Windows Vista and Windows 7.
The Windows HOSTS file allows you to block some of this content very easily and for free. However, this is not a complete internet security solution. It is still recommended that you run anti-virus software on your computer and be careful of the websites you visit.
Defining the HOSTS file
The HOSTS file is located in the following locations for the respective versions of Windows:Windows 7, Windows Vista, Windows XP, Windows Server 2003:
C:\WINDOWS\system32\drivers\etc
Windows 2000:
C:\WINNT\system32\drivers\etc\
Windows 98/ME:
C:\WINDOWS
The HOSTS file does not have an extension, but it is a plain text file. This file allows you to manually associate IP addresses with domain names (i.e., google.com) so the Domain Name Server (DNS) can quickly resolve an address.
To use the HOSTS file to block a website, assign the IP address of 127.0.0.1 to the domain name of known ad servers and malicious websites. 127.0.0.1 is the IP address of your local computer, if you chose to run a server on it.
As an example, let’s say some ad server hosts a banner ad at the URL: http://www.adsite.com/ads/12345.jpg. If you associate this domain name with the IP address of your local computer, 127.0.0.1, when that website tries to load that image, it will not be found because the image file does not exist on your computer. Therefore, the ad will not display on that webpage.
Editing the HOSTS file
Since the HOSTS file is a text file, open the file in Notepad, or other text editor, to edit it. This first line of the HOSTS file should list the local IP address:| 127.0.0.1 | localhost |
After the localhost entry, enter known ad servers and malicious websites and assign your local IP address to each domain name. Put the IP address at the beginning of the line, followed by a tab, followed by the domain name for the ad server or malicious website. Here’s an example of the HOSTS file:

NOTE: Some spyware programs automatically add ad servers and malicious websites to your HOSTS file for you.
For Windows XP/2000 users only
In Windows XP and Windows 2000, if your HOSTS file gets to large (over 135 kb), the DNS Client (a system service) will cause problems on your machine possibly causing it to lock up. This service is unnecessary and can be stopped and disabled.Therefore, before you save a big list of ad servers and malicious websites in the HOSTS file, select Control Panel | Administrative Tools | Services from the Start menu.

Scroll down to the DNS Client service, right-click on it, and select Properties from the pop-up menu.

The DNS Client Properties dialog box displays. Select Manual from the Startup type drop-down list. Click Stop below Service status to stop the service. Click Apply and then click OK.
For more information about the HOSTS file, see http://accs-net.com/hosts/what_is_hosts.html. You can find maintained HOSTS files online or start to build your own. See http://www.mvps.org/winhelp2002/hosts.htm to download a good, free, pre-populated HOSTS file.
There is a .zip file for download containing the HOSTS file, a batch file for easy installation, and a readme file with instructions for installation in the different versions of Windows. Beware that there are special instructions for Windows Vista and Windows 7.
No comments:
Post a Comment